Don't let your firm be the next big data breach headline

“We’re no longer in a situation where it’s a case of ‘if I am going to get breached’. It’s more a case of how often you are going to get breached and how long those people are going to be in for.”
These are the sobering words of cyber forensics professor Dr David Day.
His words are all the more concerning when you consider the effects that cyber-attacks have on a company. The US National Cyber Security Alliance found that 60% of SMEs are unable to sustain their business within six months of a cyber-attack. Imagine, after all the years of hard work that it has taken to progress your business, it is defunct overnight.It is extremely important, therefore, to ensure your data security is as strong as you can possibly make it. This article will outline some of the main causes of data breaches, and how you can protect yourself.
Some real-life examples
TalkTalk, the telecoms company, was hit by a cyber-attack in October 2015. The result was 157,000 customers having their personal details stolen – 15,656 of these customers had bank account numbers and sort codes stolen. The hack was widely publicised in the media and TalkTalk lost around 100,000 customers in the months immediately following the hack.
The hack is estimated to have cost TalkTalk £35m in one-off costs (such as calls into call centres and additional IT and technology costs), when you factor in the costs of lost revenue the damage is closer to £80m.
Then there’s the well-known story of Ashley Madison. A group of hackers acting as internet vigilantes hacked the website and stole the personal details of 32 million account holders. What made this hack all the more troubling is that Ashley Madison offered to fully remove user data from their servers for a one-time payment. It became clear that this was a lie when the email addresses of people who had paid to be removed turned up in the hack.
Users whose details were leaked are filing a $567 million class-action lawsuit against the parent company of Ashley Madison. The brand of Ashley Madison is now irreparably damaged. There have also been reports of a number of suicides linked to the hack.
But my company is too small to be targeted by hackers…
Understandable logic, but consider the following facts:
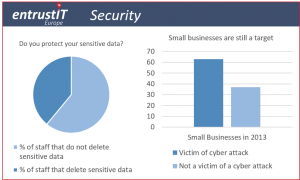
- A PwC survey found that 63 percent of small businesses were attacked by an outsider in 2013
- 57 percent of respondents to this same survey had suffered from staff-related security breaches
- IBM’s “2014 Cyber Security Intelligence Index” found that 95 percent of all security incidents involve human error. Human error can occur in businesses of all sizes, and is often painfully easy to guard against
Is burying your head in the sand really an effective protection?
Practical ways to avoid getting into trouble
Perhaps the best way to identify basic ways to protect yourself is to take a look at some of the common ways human error causes data breaches.
- 61% of staff use file sharing tools or don’t delete sensitive data
- 26% of incidents involve sending sensitive data to the wrong person
- 30% of staff click on “phishing” messages
- 12% will click on malicious email attachments
Microsoft report that 7.52% of all workstations used for web browsing remain on Windows XP and 600,000 internet connected computers run server 2003. Support for Windows XP was ended by Microsoft in 2014 – meaning that for two years all XP machines have been vulnerable to data breaches. If you’re currently sitting, red-faced, in front of your Windows XP computer – it’s time to upgrade.
Furthermore, every year a list of the most popular passwords is released. This year (2016), the top 5 were as follows:
- 123456
- password
- 12345678
- qwerty
- 12345
Yes, seriously.
So, based on the above facts, how can you be proactive about guarding against data breaches?
- Reduce transfer of data – removable storage devices should be banned outright or at least banned from transferring particularly sensitive data
- Educate your staff on how to look for phishing emails, remind them to check the email addresses they receive their mail from
- Remind staff to change their passwords regularly and ensure that they are hard to guess – preferably, insist they include at least one number and one capital letter
- Shred files – shred all sensitive files and documents once they are used
But how can you go one step further?
Whilst it is important to plug the basic holes in security, you may wish to improve your security beyond the basic level. But if you aren’t an IT expert, how can you possibly do that?
Is it time to outsource your IT for a cloud solution?
By a cloud IT solution, I am not referring to consumer cloud products such as Dropbox and iCloud. Because they are consumer products, they do not require the same security measures that a B2B solution does. I’m referring to a secure, cloud solution from a provider who makes security their top priority.
Ponder the fact that for many managing directors, IT is not their speciality. Indeed, nor is it their interest. Is updating the latest security patches on your company server likely to be high on your list of priorities? Are you likely to be constantly monitoring your server to ensure data isn’t being taken and that there are no malicious files lurking within it?
In contrast, for a cloud IT company, security is a top priority. They will be constantly monitoring their servers and they will be constantly keeping their patches up to date.
What you’re looking for
If you want confidence that your data is in safe hands, you’re looking for an IT company that can boast the following:
- ISO27001 certified – this is the industry standard of data security and is updated every year. A company with this certification has had to prove they deserve it every year they’ve had it
- Disaster Recovery/Failover built in to their systems
- At least two datacentres available to each customer for failover options
- Redundant/Resilient power and internet supplies at each datacentre
- 2 Factor Authentication options for accessing data
- Logical and physical segregation of customer applications, configuration and data
Accept nothing less.
By implementing the measures I have discussed so far, you can give your business the upper hand in the ongoing battle against hackers, and ensure that it is not your name in the next headlines.
Subscribe here!
Recent Posts
Posts by tag
- technology (128)
- Security (113)
- IT Security (100)
- cyber security (100)
- Managed Service (74)
- modern technology (71)
- Microsoft 365 (69)
- IT support (68)
- Cloud (66)
- business (63)
- cyber attack (61)
- cloud computing (60)
- cloud it (56)
- cybersecurity (56)
- microsoft (56)
- workplace (55)
- Microsoft Teams (54)
- Working from home (51)
- IT (49)
- productivity (49)
- office (46)
- office 365 (45)
- Password Security (43)
- entrustit (42)
- employees (39)
- Uncategorised (38)
- Cyber (37)
- flexible work (37)
- Remote (33)
- efficiency (31)
- Hosted Workspace (30)
- hosted desktop (30)
- it support bournemouth (30)
- schools (29)
- cyber privacy (28)
- email security (28)
- independent schools (28)
- it support dorset (27)
- school ict (27)
- collaboration (26)
- computing (26)
- 2023 (25)
- it support hampshire (25)
- public cloud (24)
- it consultancy (22)
- IT audit (21)
- entrust (20)
- it consultancy bournemouth (20)
- it support southampton (20)
- msp (20)
- password (20)
- it consultancy dorset (19)
- it consultancy hampshire (19)
- passwords (19)
- ransomware (19)
- hosted applications (18)
- it support winchester (18)
- VoIP (17)
- cloud cctv (17)
- cloud voip (17)
- covid19 (17)
- hacking (17)
- it consultancy southampton (17)
- private cloud (17)
- IT costs (16)
- data (16)
- teamwork (16)
- Coronavirus (15)
- cctv (15)
- office 365 support (15)
- GDPR (14)
- hackers (14)
- internet (14)
- network (14)
- Protection (13)
- covid-19 (13)
- hack (13)
- internet safety (13)
- management (13)
- Hosted Desktop and Applications (12)
- Windows Virtual Desktop (12)
- hardware (12)
- hybrid cloud (12)
- vulnerabilities (12)
- windows 10 (12)
- 2020 (11)
- 2022 (11)
- Microsoft Planner (11)
- artificial intelligence (11)
- awards (11)
- data breach (11)
- phishing (11)
- AI (10)
- Hampshire (10)
- IT Director (10)
- digital (10)
- uk (10)
- windows (10)
- Backup (9)
- attack (9)
- bitwarden (9)
- eu (9)
- planning (9)
- software (9)
- telephony (9)
- usecure (9)
- communication (8)
- desk phone (8)
- education (8)
- outsource (8)
- partnership (8)
- staff (8)
- Bournemouth (7)
- Cyber Essentials (7)
- Dorset (7)
- Google (7)
- OneDrive (7)
- award winning (7)
- cloud storage (7)
- european union (7)
- infrastructure (7)
- legal (7)
- mobile (7)
- offsite backup (7)
- 2019 (6)
- AI CCTV (6)
- Access Management (6)
- Apple (6)
- Cyber Essentials Plus (6)
- ISO (6)
- News (6)
- Skype for Business (6)
- apps (6)
- architect (6)
- child protection (6)
- hacks (6)
- internet of things (6)
- iot (6)
- legal it (6)
- mobile phones (6)
- onsite backup (6)
- password manager (6)
- remote desktop service (6)
- resources (6)
- virus (6)
- 3d design desktop (5)
- Azure (5)
- Case Studies (5)
- Desktop (5)
- IP (5)
- Microsoft Copilot (5)
- Multi-Site Business (5)
- Risk assessment (5)
- Thames Valley Tech & Innovation Awards (5)
- The Business Magazine (5)
- Windows 7 (5)
- award (5)
- brexit (5)
- designer (5)
- ios (5)
- legacy (5)
- modern work (5)
- personal data (5)
- smartphone (5)
- sophos (5)
- surrey (5)
- united kingdom (5)
- website (5)
- Attacks (4)
- BYOD (4)
- ChatGPT (4)
- DR (4)
- DR planning (4)
- Facebook (4)
- Government (4)
- High Growth (4)
- MDR (4)
- Managed Service Provider of the Year (4)
- Microsoft Forms (4)
- SharePoint (4)
- Tech Growth (4)
- VPN (4)
- WannaCry (4)
- Zoom (4)
- budgets (4)
- computer performance (4)
- ddos (4)
- digital transformation (4)
- disaster recovery (4)
- law (4)
- meetings (4)
- online meetings (4)
- proactive (4)
- remote learning (4)
- sme (4)
- windows 11 (4)
- wireless internet bournemouth (4)
- wireless internet southampton (4)
- 2021 (3)
- 2024 (3)
- 5G (3)
- Dorset Chamber (3)
- EDR (3)
- Fourth Industrial Revolution (3)
- General (3)
- Google Drive (3)
- Hampshire Chamber (3)
- Help (3)
- Local (3)
- Microsoft Autopilot (3)
- NHS (3)
- New Forest (3)
- South Coast Tech & Innovation Awards (3)
- Tech Company of the Year (3)
- Thames Valley (3)
- Tiva (3)
- acquisition (3)
- big switch off (3)
- citrix (3)
- closed cloud (3)
- copilot (3)
- copilot pro (3)
- digital hub (3)
- guide (3)
- innovation (3)
- instagram (3)
- intelligence (3)
- london (3)
- smart buildings (3)
- storage (3)
- strategy (3)
- teaching (3)
- trump (3)
- twitter (3)
- video conferencing tools (3)
- zero touch deployment (3)
- zero-trust (3)
- 2016 (2)
- 2018 (2)
- BGL Company (2)
- Bourne Group (2)
- Burhill (2)
- Burhill Group (2)
- CAD (2)
- Environment (2)
- Firewall (2)
- GPT-4 (2)
- Gen Z (2)
- Hampshire Business Awards (2)
- ISBA (2)
- Macs (2)
- Mr Mulligans (2)
- PaaS (2)
- Privacy Shield (2)
- Sydenhams (2)
- Wifi (2)
- XDR (2)
- afc bournemouth (2)
- afcb (2)
- android (2)
- b2b (2)
- bcs (2)
- berkshire (2)
- blockchain (2)
- broadband (2)
- camcloud (2)
- cryptocurrency (2)
- dark web (2)
- downtime (2)
- dropbox (2)
- eagle eye networks (2)
- east grinstead (2)
- exhibition (2)
- farnham (2)
- finalist (2)
- legalex (2)
- machine learning (2)
- macos (2)
- organisation (2)
- paypal (2)
- predictions (2)
- president (2)
- reading (2)
- serval systems (2)
- smart sensors (2)
- solent (2)
- us (2)
- utility management (2)
- 1998 (1)
- 2026 (1)
- AMD (1)
- ARM (1)
- Abbey Hill (1)
- Aldwickbury Park (1)
- BBC (1)
- BUNKERS! (1)
- Bedford (1)
- Bedfordshire (1)
- Birchwood Park (1)
- Burnout (1)
- CEO (1)
- Central South Business Awards (1)
- Cloud VMS (1)
- Cloudtango (1)
- Comms Dealer (1)
- East Midlands (1)
- Endpoint 100 (1)
- Go Integrator (1)
- Growth 100 (1)
- Harvey Jones Kitchens (1)
- Hoebridge (1)
- Hospitality (1)
- Ignite 2018 (1)
- Ignite 2020 (1)
- Insider (1)
- Intune (1)
- Jeff Dodd (1)
- LLM (1)
- Leaders (1)
- Loop (1)
- M&A (1)
- MFA (1)
- MPLS (1)
- MSP Select 2024 (1)
- Market (1)
- May (1)
- Multi Factor Authentication (1)
- MyAnalytics (1)
- Ninja Warrior UK (1)
- PBX (1)
- PM (1)
- Power BI (1)
- Ramsdale Park (1)
- Redbourn (1)
- Regulation (1)
- Reid Steel (1)
- SD-WAN (1)
- Surrey Business Awards (1)
- Thornbury (1)
- WCry (1)
- WannaCrypt (1)
- Windows Autopilot (1)
- Wycombe Heights (1)
- ashley madison (1)
- bandwidth (1)
- battersea (1)
- beach (1)
- big data (1)
- black friday (1)
- bloatware (1)
- brand (1)
- builders merchant (1)
- business growth (1)
- business process audit (1)
- cambridge analytica (1)
- canada (1)
- cia (1)
- clinton (1)
- cnn (1)
- co op (1)
- compliance (1)
- connectivity (1)
- copyright (1)
- crime (1)
- cyber monday (1)
- cyber resilience act (1)
- dean drako (1)
- defence (1)
- dkim (1)
- dmarc (1)
- dns (1)
- donald (1)
- dyn (1)
- election (1)
- enterprise (1)
- epos (1)
- equality (1)
- executive order (1)
- facial recognition (1)
- fax (1)
- football (1)
- gchq (1)
- grinstead (1)
- hiring (1)
- intel (1)
- intercept x (1)
- interview (1)
- josh widdicombe (1)
- knights of old (1)
- landmarks (1)
- learning (1)
- legal technology forum (1)
- leisure (1)
- meltdown (1)
- millennials (1)
- mimecast (1)
- mirai (1)
- no-deal (1)
- number plate detection (1)
- onsite (1)
- outsourcing (1)
- paper (1)
- patisserie valerie (1)
- performance reviews (1)
- pound (1)
- premier league (1)
- private equity (1)
- procrastination (1)
- qualys (1)
- recruitment (1)
- research (1)
- retail (1)
- roundtable (1)
- samsic (1)
- sharefile (1)
- smishing (1)
- snowden (1)
- solent business awards (1)
- solentBA (1)
- spectre (1)
- spf (1)
- sterling (1)
- storm (1)
- talktalk (1)
- trumppresident (1)
- ukitawards (1)
- united states (1)
- usa (1)
- vault 7 (1)
- vitality stadium (1)
- vulnerability scanning (1)
- whatsapp (1)
- white (1)
- white house (1)
- wikileaks (1)
- women in business (1)
- xiongmai (1)
- year (1)