
Phishing: All you need to know.

According to the 2018 Verizon Data Breach Investigations Report’s Phishing Statistics, 30% of phishing messages are opened by targeted users, and 12% of those users click on the malicious attachment or link.
In simple terms, phishing is a type of scam whereby cyber-criminals trick a target into doing what they want. Whether that be entering credentials into a fake website, clicking on a malicious link, or altering bank details so that payments go to fraudsters instead of the correct account.
Phishing is one of the oldest cyber threats in history as well as one of the most common forms of cyber-attack, and yet still one of the most effective. Not only is it easy to carry out but it is easy to fall for if targets do not stay vigilant. Businesses, of course, are a particularly worthwhile target to cyber-criminals.
As more and more people are using technology and therefore the internet to continue throughout the pandemic, criminals are seeing this as a special opportunity to release attacks on unsuspecting users. In April 2020, Security Boulevard found a 600% rise in phishing campaigns. Such criminals are using coronavirus to their advantage and are disgusting their emails to appear as if they are being sent by medical authorities such as the World Health Organisation (WHO) – a topical organisation amid the worldwide pandemic.
With so much uncertainty in the world economy in 2020/1, it has never been more important for businesses to stay protected from devastating attacks by learning about phishing and how scammers use it to exploit their victims. The effects of phishing attacks can be detrimental, let alone when the world isn’t amid a global pandemic. IBM reports that the average successful phishing attack costs a company an average of £3m.
By pooling on our knowledge of cyber-security over the past decade and what we have seen throughout the pandemic so far, we have put together this guide on phishing to provide you with useful information which will help prevent your business from becoming a victim.
What is phishing?
A phishing attack occurs when a scammer attempts to trick victims into giving away personal information. Data wanted by such scammers can range from personal or corporate emails and passwords, to financial information such as credit card details or online banking credentials. Once in the hands of cyber-criminals, it can be used for several reasons. For example, to be sold on the dark web (an overlay of networks that requires specific tools and software in order to gain access), to buy things, or for identity theft. In some cases, it is even used for blackmail or to embarrass victims.
Phishing is also a popular way for cyber-criminals to deliver malware to victims, by encouraging them to click on a link or download an attachment. Both actions would spread malware and other malicious content onto the device which could result in company data being held for ransom.
Anyone can be a target of phishing attack, and all it takes is an uniformed employee to click on a malicious link or enter their details into a fake webpage for your business to become the next victim.
How does a phishing attack work?
Over the years, we have all become familiar with the classic spam email and learnt how to dodge them. However, phishing emails can look deceivingly credible. Advances in technology have resulted in cyber-criminals becoming more sophisticated than ever before. As a result, they have found new ways to evolve old-age techniques and make their disguises even harder to uncover.
The precise mechanics of each scam varies. However, usually via email, phone or text, cyber-criminals will manipulate users into trusting them so that they hand over or enter valuable information. For example, the target may be tricked into clicking on a link which takes them to a fake web page. The aim here would be for the target to enter any personal information which can then be stolen. This method is regularly used with PayPal scammers, whereby they instruct targets to click on a link to rectify a discrepancy with their account. The link redirects to a fake PayPal login page which collects the victim’s credentials and sends them to the scammer.
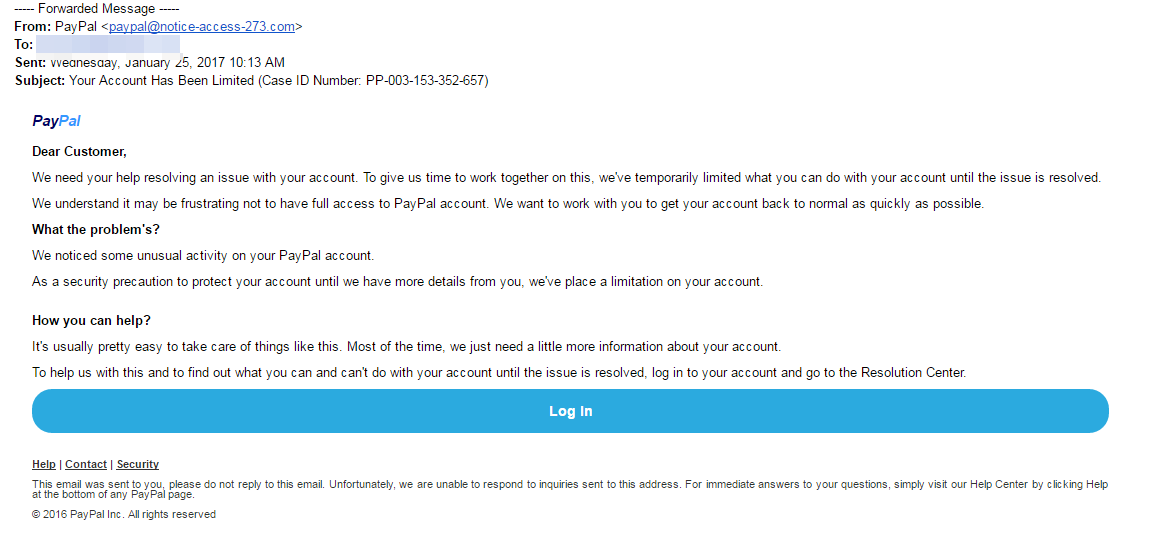
Email tends to be most common method of performing phishing attacks due to the sheer number of emails that are sent every day. Experts estimate that 3.7 billion people sent around 269 billion emails every single day. Symantec research suggests that nearly one in every 2,00 of these emails are a phishing email, meaning roughly 135 million phishing attacks are attempted every day.
What about spear phishing?
Spear phishing is far more of an advanced and precise attack than regular phishing, which is more of a dragnet strategy. Fraudsters use social engineering techniques with spear phishing to aim messages at specific organisations or individuals. For example, cyber-criminals will collect information of their target over time, then craft the email with the target’s name, position, company and much more to deceive the recipient into thinking they have a connection with the sender. In these attacks they spoof the sender name so that it appears as if the email or text is coming from someone they trust, e.g. their company CEO or another executive.
A common example of spear phishing we see among businesses is when an employee receives an email from their ‘boss’ asking for them to process a bank transfer. It will almost always include some form of urgency and say that they are busy as this means someone is less likely to follow it up. While it appears to come from their ‘boss’, it is in fact a cyber-criminal who has spoofed the email. Emails like this should always be followed up with a phone call to your boss or the ‘sender’ if possible.
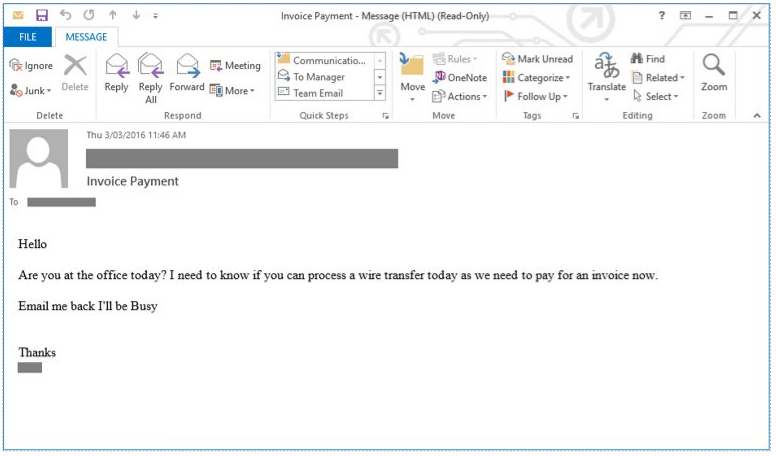
Although these types of scams take more effort, there is normally a bigger potential payback for fraudsters. It is spear phishing attacks that have been used as entry point for a number of high-profile cyber-attacks and breaches. For instance, only recently did we see Twitter confirm its employees were tricked into giving hackers their credentials, which gave them access to the accounts of Bill Gates Jeff Bezos, Joe Biden, and others.
What about Business Email Compromise?
If you’re a business, there is also the chance that cyber-criminals will attempt to appear as your business to scam customers and others close to you. Known as Business Email Compromise (BEC), this form of targeted phishing attack has been on the rise over recent years and has been very successful.
The impacts of BEC can go far beyond monetary loss – the reputational damage is far more concerning. For example, if an email appeared to have come from your business which scammed a customer or installed malware onto their device, they may no longer trust you and pass on their bad experience onto others. In a study of 2,000 survey participants, nearly 87% said they would not (or were not very likely to) do business with a company that has faced a data breach involving credit or debit card information.
Fortunately, as part of our commitment to providing proactive IT support, we introduced Domain-based Message Authentication, Reporting & Conformance (DMARC) to our portfolio of services. Since then, it has been successful in helping prevent cyber-criminals from appearing as businesses. You can find out more about it here.
How can you stay protected?
Regardless of the technology or target, deception will always be at the core of phishing attacks. Therefore, training, training and more training on phishing attacks and how to spot one is key when trying to stay protected.
While some phishing emails are so sophisticated that even the message looks authentic, there are some key giveaways which will make it clear that it is in fact an attempted attack. Some of these include:
- Legitimate organisations won’t request sensitive information via email
- Most organisations will not send you an email requesting passwords, credit card details, or anything else personal, nor will them send you a link from which you need to login. So, if you receive an unsolicited email from an organisation including a link or attachment which asks you to provide sensitive data, the chances are it is a scam.
- Legitimate organisations will usually call you by your name
- Typically, phishing emails will use generic greetings such as “Dear valued member”, “Dear account holder” or “Dear customer”. However, some hackers avoid this all together or with spear phishing will use first name, so it is always worth checking other elements of the email. More on that is below.
- Legitimate organisations have domain emails
- Don’t just check the name of the person sending the email – these can easily be changed. Check the email address by hovering your mouse over the ‘from’ address. If these do not match and the ‘from’ address looks shady or has alterations, it is probably a phishing email.
- Legitimate organisations know how to spell
- Probably one of the easiest give-aways – if an email has bad grammar and spelling. Emails from legitimate organisations are normally well written. According to experts, there’s actually purpose behind this. Scammers prey on those uneducated, believing them to be less observant and therefore, easier targets.
- Legitimate organisations don’t send unsolicited attachments
- In general terms, authentic organisations won’t randomly send you an email with an attachment but would instead direct you to download documents or files on their own website. However, this isn’t always the case. Ensure you keep an eye out for high-risk attachment file types which include .exe, .scr and .zip. If in doubt, contact the company using contact information from their website.
- Legitimate organisation links match legitimate URLs
- Just because a link says it will take you somewhere, doesn’t mean it actual will. By hovering over the link you can double check the URL. If the link doesn’t seem correct or match the context of the email, don’t click on it.
Phishing may be one of the longest standing cyber-threats, but it remains one of the most prevalent threats for two reasons – it is easy to carry out, and it works because there are still plenty of people who use internet simply unaware of the threats they are faced with.
So, no matter if you have the most secure security protections in place, all it takes is one untrained employee to be caught out by a phishing attempt. Even some of the most advanced users can make mistakes on occasion. Cyber-security training for your workforce will never be a wasted investment, and by following the simple tips, knowledge and advice outlined in this guide, you too can help to minimise the threat to your organisation.
entrustIT have over 16 years of experience in the cyber security sector. We have helped many businesses over this time to protect against phishing attacks and prevent the devasting impacts they can have if successful. Whether that be using our knowledge to provide training for you and your employees or implementing security solutions such as DMARC, we can proactively assist you throughout the pandemic and beyond.
Please get in touch with a member of the team on 0330 002 0045 or email enquiries@entrustit.co.uk if you think you could benefit.
Subscribe here!
Recent Posts
Posts by tag
- technology (129)
- Security (113)
- IT Security (100)
- cyber security (100)
- Managed Service (74)
- modern technology (71)
- Microsoft 365 (69)
- IT support (68)
- Cloud (66)
- business (64)
- cyber attack (61)
- cloud computing (60)
- cloud it (56)
- cybersecurity (56)
- microsoft (56)
- workplace (55)
- Microsoft Teams (54)
- Working from home (51)
- IT (50)
- productivity (49)
- office (46)
- office 365 (45)
- Password Security (43)
- entrustit (42)
- employees (39)
- Uncategorised (38)
- Cyber (37)
- flexible work (37)
- Remote (33)
- efficiency (31)
- Hosted Workspace (30)
- hosted desktop (30)
- it support bournemouth (30)
- schools (29)
- cyber privacy (28)
- email security (28)
- independent schools (28)
- it support dorset (27)
- school ict (27)
- collaboration (26)
- computing (26)
- 2023 (25)
- it support hampshire (25)
- public cloud (24)
- it consultancy (22)
- IT audit (21)
- entrust (20)
- it consultancy bournemouth (20)
- it support southampton (20)
- msp (20)
- password (20)
- it consultancy dorset (19)
- it consultancy hampshire (19)
- passwords (19)
- ransomware (19)
- hosted applications (18)
- it support winchester (18)
- VoIP (17)
- cloud cctv (17)
- cloud voip (17)
- covid19 (17)
- hacking (17)
- it consultancy southampton (17)
- private cloud (17)
- IT costs (16)
- data (16)
- teamwork (16)
- Coronavirus (15)
- cctv (15)
- network (15)
- office 365 support (15)
- GDPR (14)
- hackers (14)
- internet (14)
- Protection (13)
- covid-19 (13)
- hack (13)
- internet safety (13)
- management (13)
- Hosted Desktop and Applications (12)
- Windows Virtual Desktop (12)
- hardware (12)
- hybrid cloud (12)
- vulnerabilities (12)
- windows 10 (12)
- 2020 (11)
- 2022 (11)
- Microsoft Planner (11)
- artificial intelligence (11)
- awards (11)
- data breach (11)
- phishing (11)
- AI (10)
- Hampshire (10)
- IT Director (10)
- digital (10)
- uk (10)
- windows (10)
- Backup (9)
- attack (9)
- bitwarden (9)
- eu (9)
- planning (9)
- software (9)
- telephony (9)
- usecure (9)
- communication (8)
- desk phone (8)
- education (8)
- infrastructure (8)
- outsource (8)
- partnership (8)
- staff (8)
- Bournemouth (7)
- Cyber Essentials (7)
- Dorset (7)
- Google (7)
- OneDrive (7)
- award winning (7)
- cloud storage (7)
- european union (7)
- legal (7)
- mobile (7)
- offsite backup (7)
- 2019 (6)
- AI CCTV (6)
- Access Management (6)
- Apple (6)
- Cyber Essentials Plus (6)
- IP (6)
- ISO (6)
- News (6)
- Skype for Business (6)
- apps (6)
- architect (6)
- child protection (6)
- hacks (6)
- internet of things (6)
- iot (6)
- legal it (6)
- mobile phones (6)
- onsite backup (6)
- password manager (6)
- remote desktop service (6)
- resources (6)
- virus (6)
- 3d design desktop (5)
- Azure (5)
- Case Studies (5)
- Desktop (5)
- Microsoft Copilot (5)
- Multi-Site Business (5)
- Risk assessment (5)
- Thames Valley Tech & Innovation Awards (5)
- The Business Magazine (5)
- Windows 7 (5)
- award (5)
- brexit (5)
- designer (5)
- ios (5)
- legacy (5)
- modern work (5)
- personal data (5)
- smartphone (5)
- sophos (5)
- surrey (5)
- united kingdom (5)
- website (5)
- Attacks (4)
- BYOD (4)
- ChatGPT (4)
- DR (4)
- DR planning (4)
- Facebook (4)
- Government (4)
- High Growth (4)
- MDR (4)
- Managed Service Provider of the Year (4)
- Microsoft Forms (4)
- SharePoint (4)
- Tech Growth (4)
- VPN (4)
- WannaCry (4)
- Zoom (4)
- budgets (4)
- computer performance (4)
- ddos (4)
- digital transformation (4)
- disaster recovery (4)
- law (4)
- meetings (4)
- online meetings (4)
- proactive (4)
- remote learning (4)
- sme (4)
- windows 11 (4)
- wireless internet bournemouth (4)
- wireless internet southampton (4)
- 2021 (3)
- 2024 (3)
- 5G (3)
- Dorset Chamber (3)
- EDR (3)
- Fourth Industrial Revolution (3)
- General (3)
- Google Drive (3)
- Hampshire Chamber (3)
- Help (3)
- Local (3)
- Microsoft Autopilot (3)
- NHS (3)
- New Forest (3)
- South Coast Tech & Innovation Awards (3)
- Tech Company of the Year (3)
- Thames Valley (3)
- Tiva (3)
- acquisition (3)
- big switch off (3)
- citrix (3)
- closed cloud (3)
- copilot (3)
- copilot pro (3)
- digital hub (3)
- guide (3)
- innovation (3)
- instagram (3)
- intelligence (3)
- london (3)
- smart buildings (3)
- storage (3)
- strategy (3)
- teaching (3)
- trump (3)
- twitter (3)
- video conferencing tools (3)
- zero touch deployment (3)
- zero-trust (3)
- 2016 (2)
- 2018 (2)
- BGL Company (2)
- Bourne Group (2)
- Burhill (2)
- Burhill Group (2)
- CAD (2)
- Environment (2)
- Firewall (2)
- GPT-4 (2)
- Gen Z (2)
- Hampshire Business Awards (2)
- ISBA (2)
- Macs (2)
- Mr Mulligans (2)
- PaaS (2)
- Privacy Shield (2)
- Sydenhams (2)
- Wifi (2)
- XDR (2)
- afc bournemouth (2)
- afcb (2)
- android (2)
- b2b (2)
- bcs (2)
- berkshire (2)
- blockchain (2)
- broadband (2)
- camcloud (2)
- cryptocurrency (2)
- dark web (2)
- downtime (2)
- dropbox (2)
- eagle eye networks (2)
- east grinstead (2)
- exhibition (2)
- farnham (2)
- finalist (2)
- legalex (2)
- machine learning (2)
- macos (2)
- organisation (2)
- paypal (2)
- predictions (2)
- president (2)
- reading (2)
- serval systems (2)
- smart sensors (2)
- solent (2)
- us (2)
- utility management (2)
- 1998 (1)
- 2026 (1)
- AMD (1)
- ARM (1)
- Abbey Hill (1)
- Aldwickbury Park (1)
- BBC (1)
- BUNKERS! (1)
- Bedford (1)
- Bedfordshire (1)
- Birchwood Park (1)
- Burnout (1)
- CEO (1)
- Central South Business Awards (1)
- Cloud VMS (1)
- Cloudtango (1)
- Comms Dealer (1)
- East Midlands (1)
- Endpoint 100 (1)
- Go Integrator (1)
- Growth 100 (1)
- Harvey Jones Kitchens (1)
- Hoebridge (1)
- Hospitality (1)
- Ignite 2018 (1)
- Ignite 2020 (1)
- Insider (1)
- Intune (1)
- Jeff Dodd (1)
- LLM (1)
- Leaders (1)
- Loop (1)
- M&A (1)
- MFA (1)
- MPLS (1)
- MSP Select 2024 (1)
- Market (1)
- May (1)
- Multi Factor Authentication (1)
- MyAnalytics (1)
- Ninja Warrior UK (1)
- PBX (1)
- PM (1)
- Power BI (1)
- Ramsdale Park (1)
- Redbourn (1)
- Regulation (1)
- Reid Steel (1)
- SD-WAN (1)
- Surrey Business Awards (1)
- Thornbury (1)
- WCry (1)
- WannaCrypt (1)
- Windows Autopilot (1)
- Wycombe Heights (1)
- ashley madison (1)
- bandwidth (1)
- battersea (1)
- beach (1)
- big data (1)
- black friday (1)
- bloatware (1)
- brand (1)
- builders merchant (1)
- business growth (1)
- business process audit (1)
- cambridge analytica (1)
- canada (1)
- cia (1)
- clinton (1)
- cnn (1)
- co op (1)
- compliance (1)
- connectivity (1)
- copyright (1)
- crime (1)
- cyber monday (1)
- cyber resilience act (1)
- dean drako (1)
- defence (1)
- dkim (1)
- dmarc (1)
- dns (1)
- donald (1)
- dyn (1)
- election (1)
- enterprise (1)
- epos (1)
- equality (1)
- executive order (1)
- facial recognition (1)
- fax (1)
- football (1)
- gchq (1)
- grinstead (1)
- hiring (1)
- intel (1)
- intercept x (1)
- interview (1)
- josh widdicombe (1)
- knights of old (1)
- landmarks (1)
- learning (1)
- legal technology forum (1)
- leisure (1)
- meltdown (1)
- millennials (1)
- mimecast (1)
- mirai (1)
- no-deal (1)
- number plate detection (1)
- onsite (1)
- outsourcing (1)
- paper (1)
- patisserie valerie (1)
- performance reviews (1)
- pound (1)
- premier league (1)
- private equity (1)
- procrastination (1)
- qualys (1)
- recruitment (1)
- research (1)
- retail (1)
- roundtable (1)
- samsic (1)
- sharefile (1)
- smishing (1)
- snowden (1)
- solent business awards (1)
- solentBA (1)
- spectre (1)
- spf (1)
- sterling (1)
- storm (1)
- structured cabling (1)
- talktalk (1)
- trumppresident (1)
- ukitawards (1)
- united states (1)
- usa (1)
- vault 7 (1)
- vitality stadium (1)
- vulnerability scanning (1)
- whatsapp (1)
- white (1)
- white house (1)
- wikileaks (1)
- women in business (1)
- xiongmai (1)
- year (1)


